Allow Connections and Configure Firewall
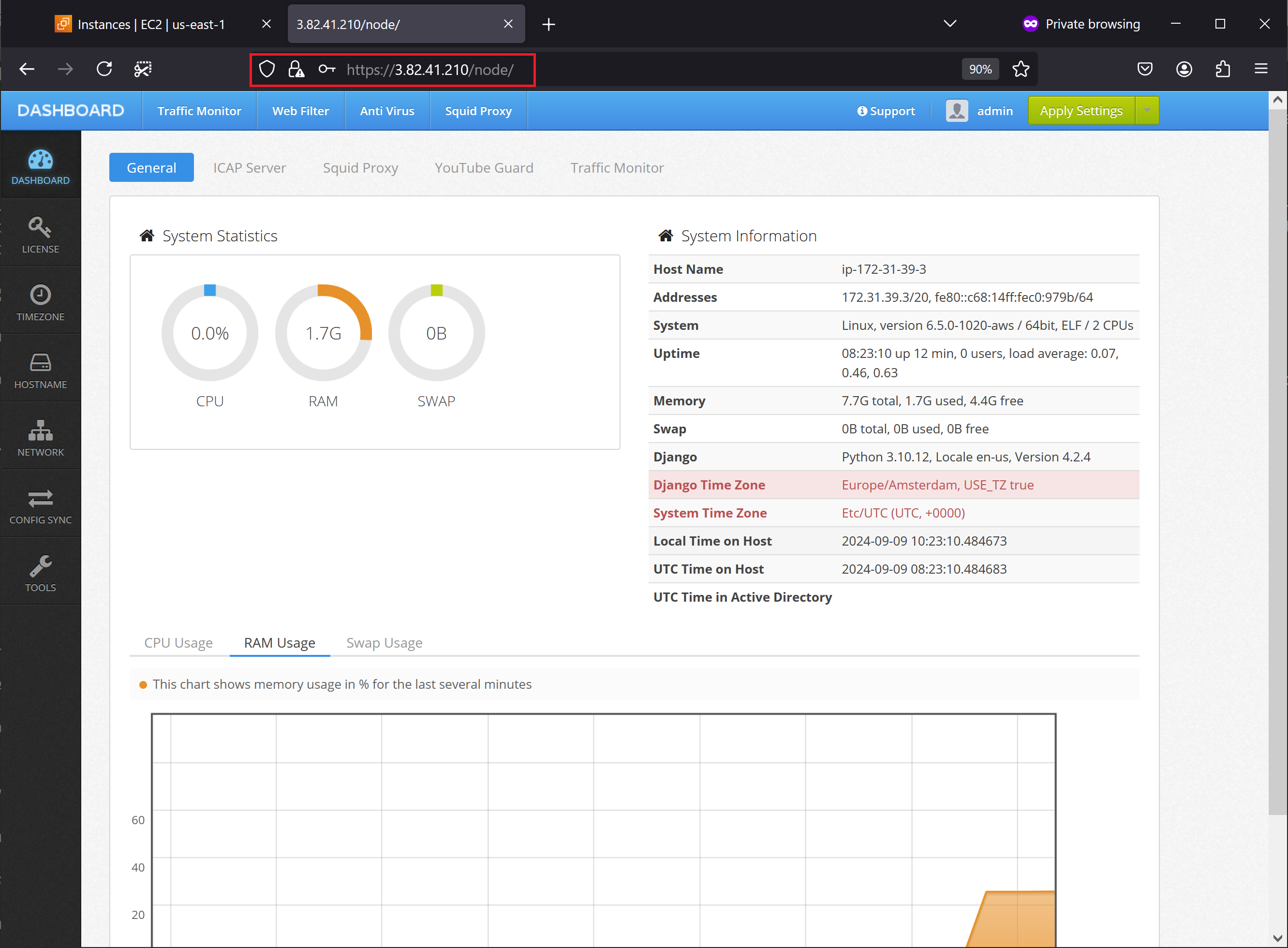
Open the browser and navigate to IP address of the running virtual machine (port 443, protocol HTTPS). You should see the Admin Console UI of Web Safety. Type default admin user name and the virtual machine instance ID as password (in our case it is i-0542754f04f0820e5) to see the Dashboard.
Important
Note, it is possible you will get the Warning: Potential Security Risk Ahead message from the browser, this is because the Admin UI uses self-signed TLS certificate to protect access to itself. You can temporary Accept the risk and continue for this connection and setup usual TLS certificate later as explained in the documentation.
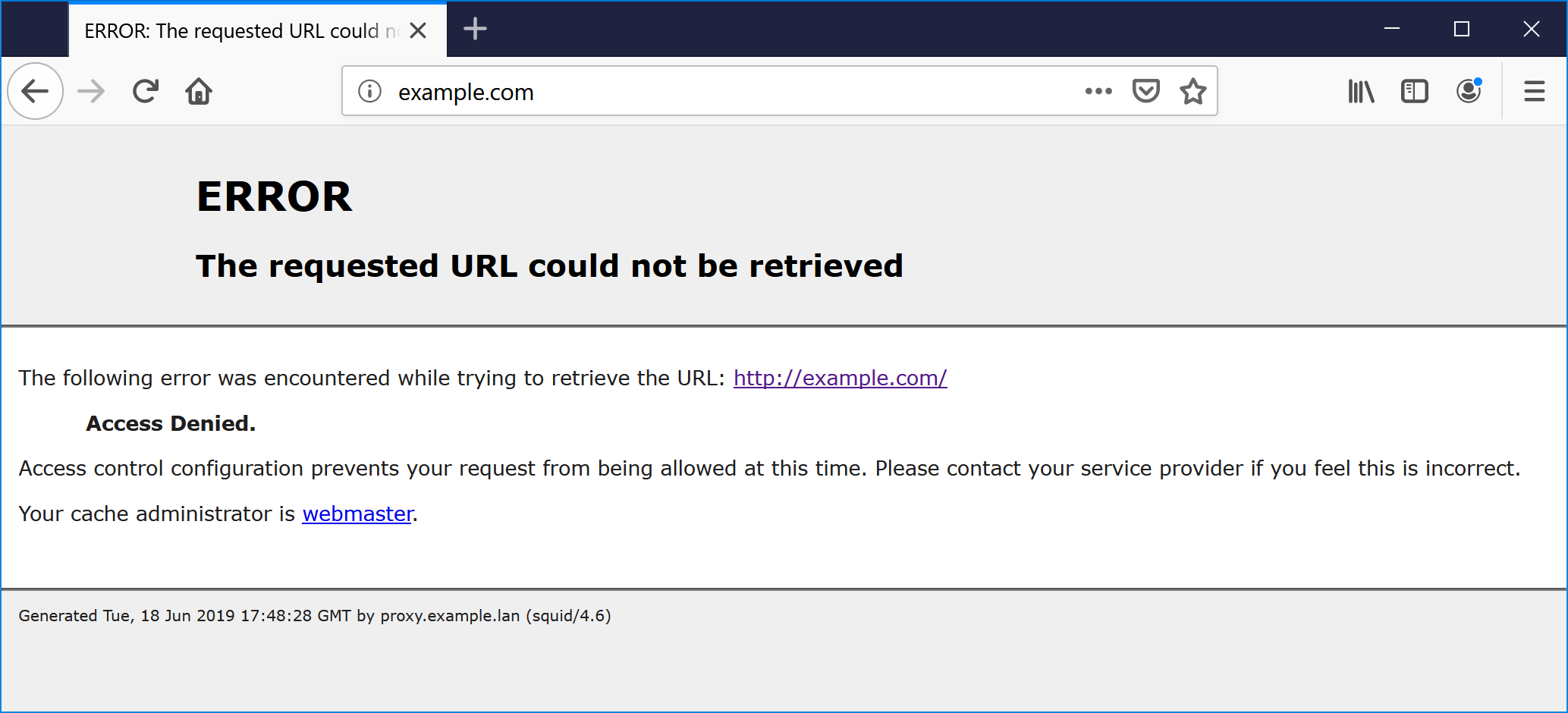
By default, proxy allows connections from internal LAN IP address ranges only (addresses like 192.168.1.0/24). When our browser is set to talk to proxy in the cloud its visible IP address will be public (set by your ISP provider) and thus will be denied. Typically, the following reply page will indicate a denied access.
ERROR
The requested URL could not be retrieved
The following error was encountered while trying to retrieve the
URL: http://example.com/
Access Denied.
Access control configuration prevents your request from being allowed
at this time. Please contact your service provider if you feel
this is incorrect.
Your cache administrator is webmaster.
Generated Tue, 18 Jun 2019 17:48:28 GMT by proxy.example.lan (squid/4.6)
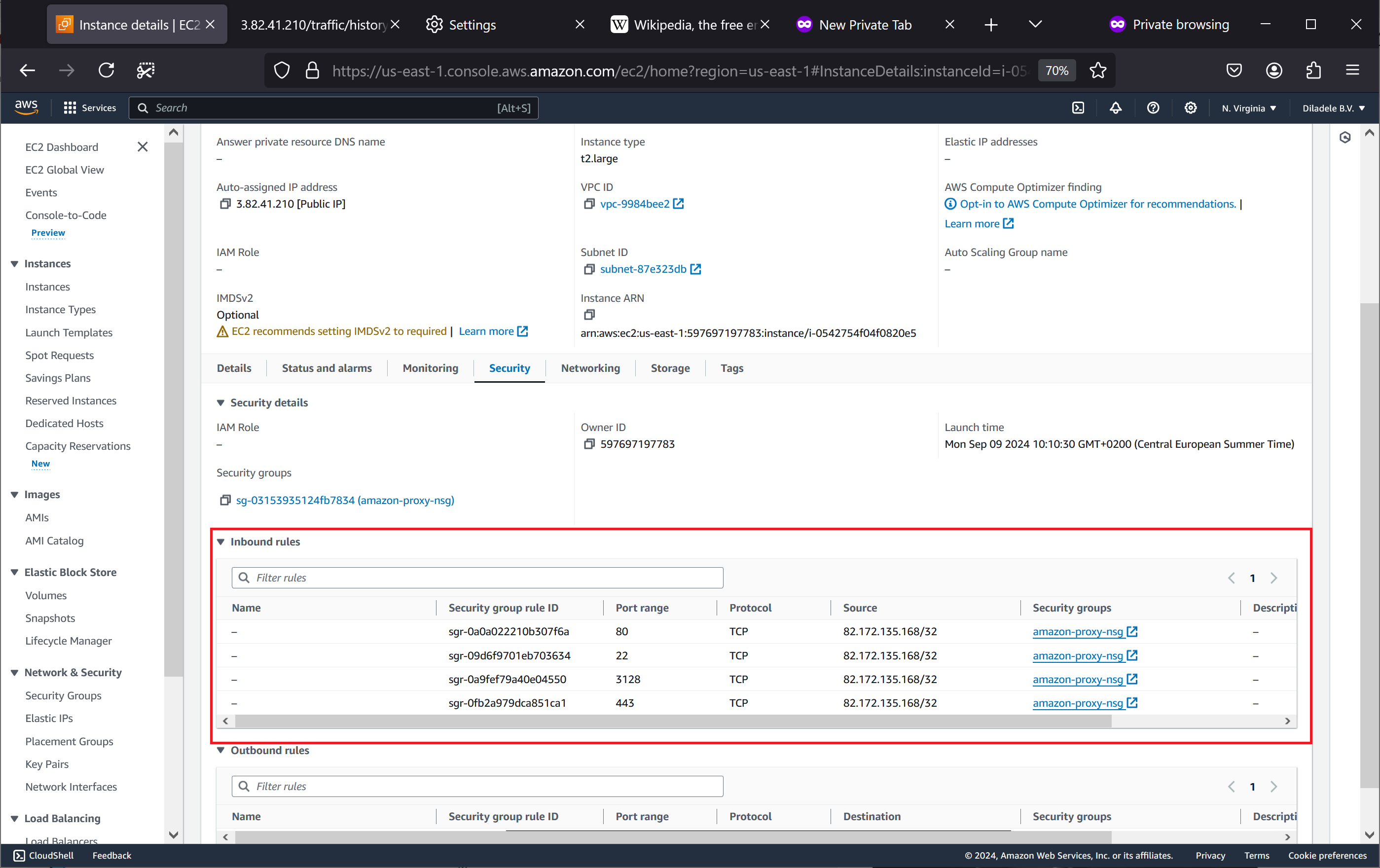
Allow Connections from Your IP
If you have a static public IP address set by your provider, then it is a good idea to limit the incoming connections to the proxy only from this public IP address using the Network Security Group firewall rules in the Amazon AWS as shown below.
After that, open the Admin UI of Web Safety, navigate to Squid Proxy / Settings / Default ACLs and type the following directives.
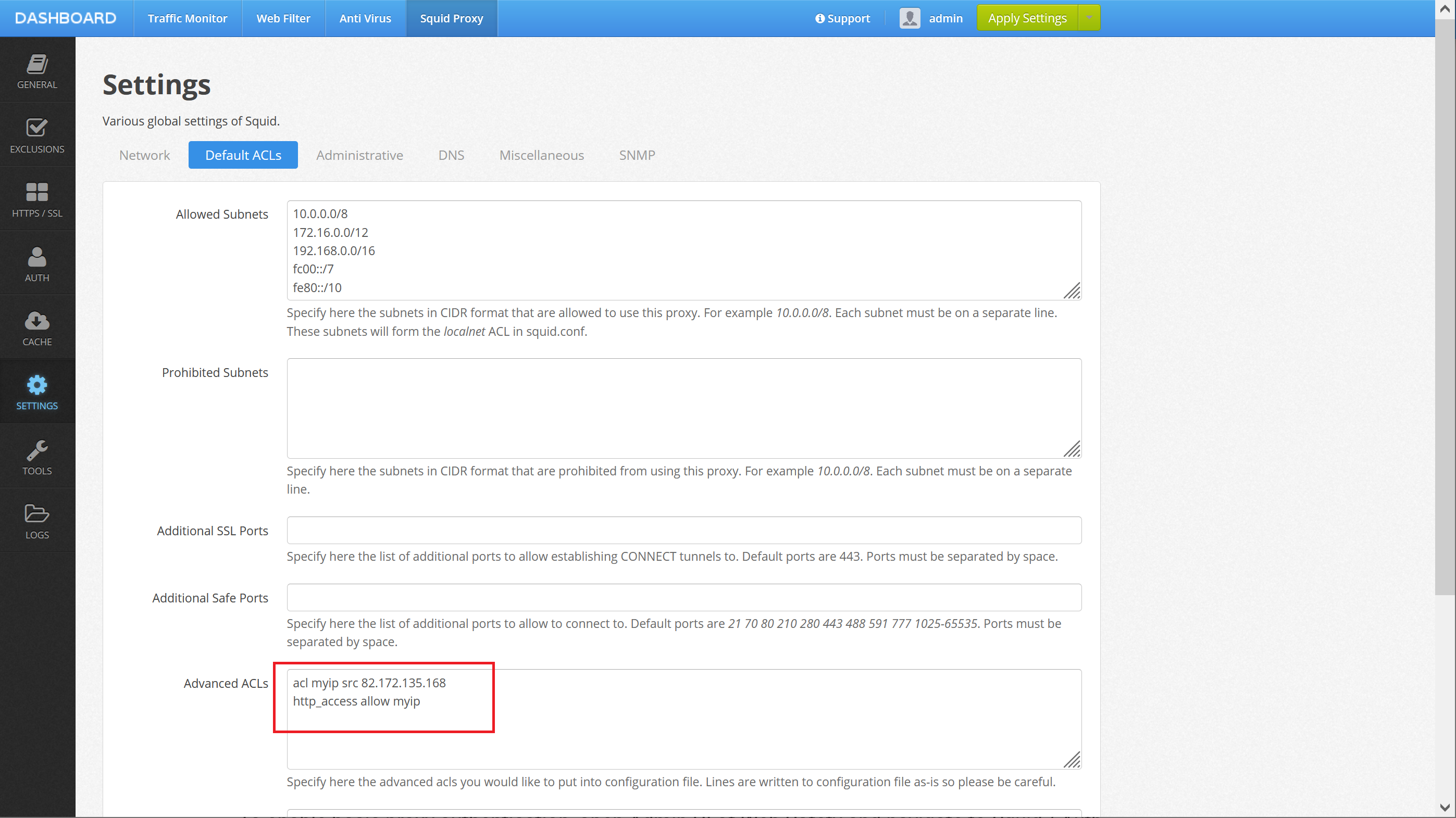
This will allow connections to the proxy from this given public IP address only.
Require All Connections to Authenticate
It is also possible to configure proxy to accept all connecting users and require them to authenticate themselves, for example using Basic Authentication. This step is properly described in the Proxy Authentication section of this Admin Guide.